mirror of
https://github.com/dani-garcia/vaultwarden.git
synced 2026-02-05 00:29:40 +03:00
Bitwarden Container does not start with newly generated certificates #387
Reference in New Issue
Block a user
Delete Branch "%!s()"
Deleting a branch is permanent. Although the deleted branch may continue to exist for a short time before it actually gets removed, it CANNOT be undone in most cases. Continue?
Originally created by @seehma on GitHub (Aug 25, 2019).
Hi,
hope iam not discussing an allready discussed issue but i have problems with my newly generated letsencrypt certificates. Those certificates are working well on a nextcloud container but not in bitwarden.
I have version 1.9.1 running on docker on a Synology NAS. With the old certificates it is working fine (they are in the same directory just renamed cert.pem_working and privkey.pem_working).
However i have in the same directory the new generated certificates and with them the bitwarden container wont start anymore. I get the following error:
Again if i switch to my old certificates which are located right beside the new ones, everything works fine.
Iam also using the same certificates for my synology NAS and there they are also working fine.
Thats my settings:
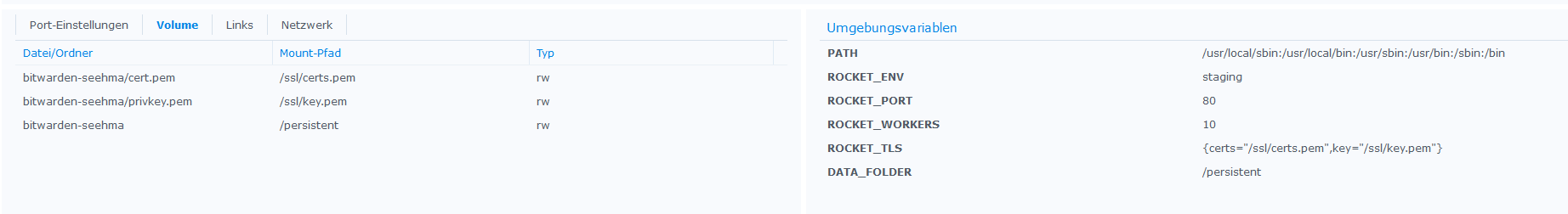
Any suggestions?
Thx for help in advance!
M.
@Ayitaka commented on GitHub (Aug 25, 2019):
According to the Rocket source code...
Sounds like something is wrong the with private key. (Maybe copied the wrong file?) Double check that the format of the private key is correct starting with:
then long lines of equally sized text, and ending with:
Lets Encrypt apparently issues PKCS#10 PEM formatted certificates, according to their API documentation, but since their default certs work fine for me and others I have to assume it has nothing to do with the "key in either PKCS#1 or PKCS#8" bit.
Just some places to start checking, sorry I can't be more specific with an answer for you.
@seehma commented on GitHub (Aug 31, 2019):
Hi, i checked if the file has the right beginning and ending. The only difference was that i had
-----BEGIN RSA PRIVATE KEY-----I tried to change this to
-----BEGIN PRIVATE KEY-----and of course the same on the end of the file, but i get the same error message again.
One more difference to the old working certificates is that the cert.pem file has to begin and end blocks. i dont know why but as i said in Nextcloud it is working perfectly fine.
@seehma commented on GitHub (Aug 31, 2019):
Hi, i tried some more things including a new certificate with a new subdomain and this works now. The other certificate was valid for two domains -> bw.mydomain.at and secondname.mydomain.at
The new certificate is only valid for bw2.mydomain.at and now it looks like this is ok for bitwarden (ROCKET_TLS).